HNSort.com is an app I threw together this weekend that allows readers to sort the stories on Hacker News by various criteria (rank, points, comments, title, domain, submitter, and age).
This mini project spawned from two frustrations: 1) my dissatisfaction with the interface for reading the site 2) a desire to have an atomic project that I could complete and be done with in a weekend.
I check HN periodically throughout the day in between tasks. But rather than reading every headline I skim the site to find the posts that are most important (as indicated by a high number of comments and points). Unfortunately there’s no easy way to find those gem posts, you end up having to sift through each post. So in the spirit of the site itself (ie. hacking stuff to make it work they way you want) I wrote a different interface for it. For anyone interested in the details I’ll explain below how the app works and the backstory on how I made it.
The backstory
The main goal was to get a convenient way to quickly find the gems on Hacker News without having to manually skim through each story. Ideally I wanted something that would work both on my computer as well as my iPhone. And as a bonus I thought it would be neat to expose it so others could use it, and in so doing provide us some cheap, targeted advertising for JumpBox to an audience that would appreciate it. I knew given the nature of the app that it would probably do well on HN itself.
I looked briefly into what it would take to write a Greasemonkey FF extension but my javascript skills are wretched and even if I were able to make that work, it wouldn’t help for reading on the iPhone nor would there be any promo benefit to JumpBox. So I concluded it would need to be a mashup that was accessible via the web.
There is no public API to HN so the first step was to create one using Dapper. This was the easiest part of the whole project. Their wizard makes it ridiculously easy to turn any webpage into a feed of XML, JSON, RSS, whatever you need. It took all of five minutes to make this dapp to produce a real-time XML feed of stories off their homepage. So far so good.
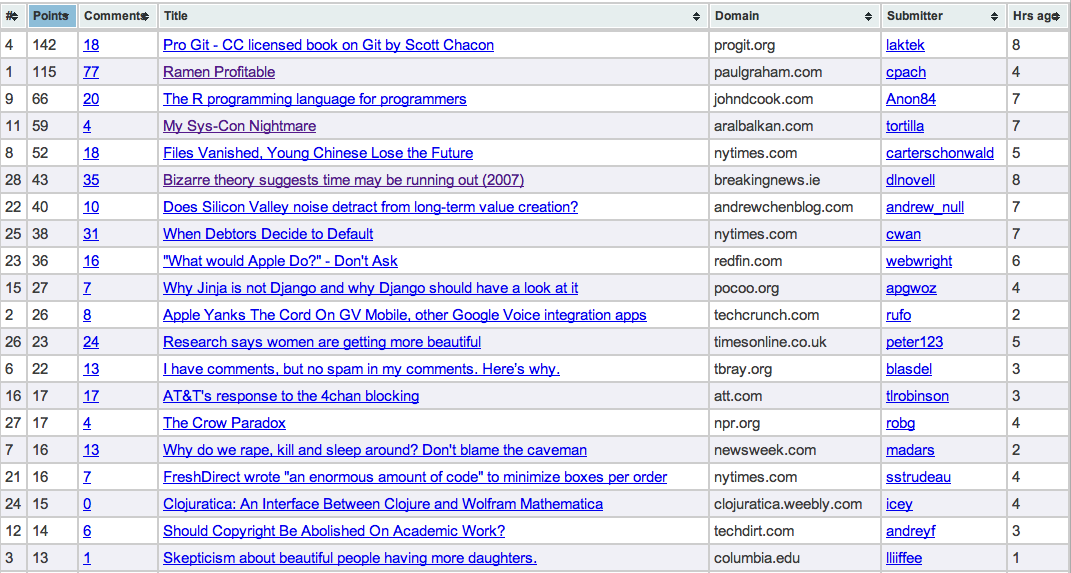
The next thing I tried was to head over to Mindtouch and fire up a free express account and use their Mindtouch Core product to render the results in a sortable table. Again this took all of five minutes to produce this result which was promising but lacked the sorting capability. Unfortunately adding the sorting feature would prove to be significantly more difficult. After a few hours of tinkering with Dekiscript (their proprietary scripting language) I eventually gave up – I’m sure there is a way to iterate over an XML result set using Dekiscript but I certainly couldn’t figure it out even with a ton of good documentation.
At this point I tried one last gasp effort to solve this using a free pre-made tool: I knew Google Spreadsheets had the ability to import XML and JSON feeds. And a Google Spreadsheet can be sorted six ways from Sunday so all good there. Hopeful about this avenue, I went and tinkered for about an hour trying to get the import to work per the Google documentation but sadly had to give up. Apparently Google just didn’t like the XML feed. Sigh.
Having run out of options I decided at this point to dust off the Coldfusion skills and try to code this thing from scratch. What would have been ideal at this point would have been a JumpBox for Railo or BlueDragon. Instead I futzed around trying to find an online sandbox where I could develop without having to install anything on my Mac. I opened an account here but sadly the CFHTTP tag I needed to use was malfunctioning on their system. I then opened up a $5/mo hosting account with Hostek only to learn that they disable the CFDUMP tag which is key when developing with nested structures and result sets. I ended up installing the standalone from Adobe on my Mac and making the site there.
After a few hours of tinkering I had it consuming and displaying the results in a table. There was another hour of scrubbing and transforming the data so all the numbers were sortable. The last step was to add in the Tablesorter jQuery plugin. And the final result was exactly what I wanted: a simple HTML spreadsheet of all the articles on the homepage of HN. For you coders here’s the single page of code that handles everything.
Granted this ended up occupying most of my weekend but it was a great exercise in learning about a bunch of different technologies. I submitted the page to Hacker News and it rose to #3 on the homepage last night with significant momentum. Sadly when I woke up this morning my provider had experienced a DNS outage rendering the site unreachable since last night and therefore cutting it down while it was in its prime. You only get one shot at the homepage of HN so I have no idea how people will find it now :-(
But all in all a good learning experience with an output that I can (and will) use from now on for reading that site. At $5/mo it’s worth it to me for my personal use alone. And the good news is that it even works on the iPhone. If you’re a fan of HN try it for reading that site and tell me what you think.
 It can’t be assumed it will reach its intended recipient.
It can’t be assumed it will reach its intended recipient. 
 Here’s ten things I predict we’ll see in the IT/computing industry in 2010 (and yes, I’m biased about some given the world we live in at
Here’s ten things I predict we’ll see in the IT/computing industry in 2010 (and yes, I’m biased about some given the world we live in at  Here’s an interesting debate we had this morning in our office:
Here’s an interesting debate we had this morning in our office: 






